
The internet has become the lifeblood of every individual and business in this disrupting digital world, triggered by the pandemic. Organizations have been forced into changing their working practices with a majority of them establishing remote work or Work from Home (WFH) for their employees. This unexpected switch has seen a massive spike in cyberattacks and hackers are seizing every opportunity to take advantage of the situation.
Hacktivists are stepping up their cybercriminal activities by exploiting human psychology to trick individuals into handing over valuable personal and company data. They are utilizing "social engineering" to commit high-value cybercrimes. Although the pandemic is certainly not the first occurrence of such attacks, this phase has brought them into the mainstream of sophisticated cyber threatscape. According to KnowBe4, only about 3% of malware tries to exploit an exclusively technical flaw. The other 97% instead targets users through Social Engineering.
What is Social Engineering?
In simple terms, social engineering is the act of deceiving or manipulating someone into divulging confidential or personal information that may be used for malicious activities.
Attackers use social engineering tactics to exploit people's natural tendency to trust others. Such attacks rely heavily on human interaction, and they are all about the "psychology of persuasion". The attacker fabricates a false sense of security and trust with the unsuspecting users or employees, then encourages them into taking unsafe actions. For this reason of human manipulation, it is also considered "human hacking". Many social engineering attacks exploit basic human cognitive functions like people's willingness to be helpful, curiosities to experience new things, fears, etc.
Social engineering attackers are called social engineers. Their physiological tricks can break the strength of even the best security systems.
How Does a Social Engineering Attack Work?
This simple figure illustrates the typical lifecycle of a social engineering attack: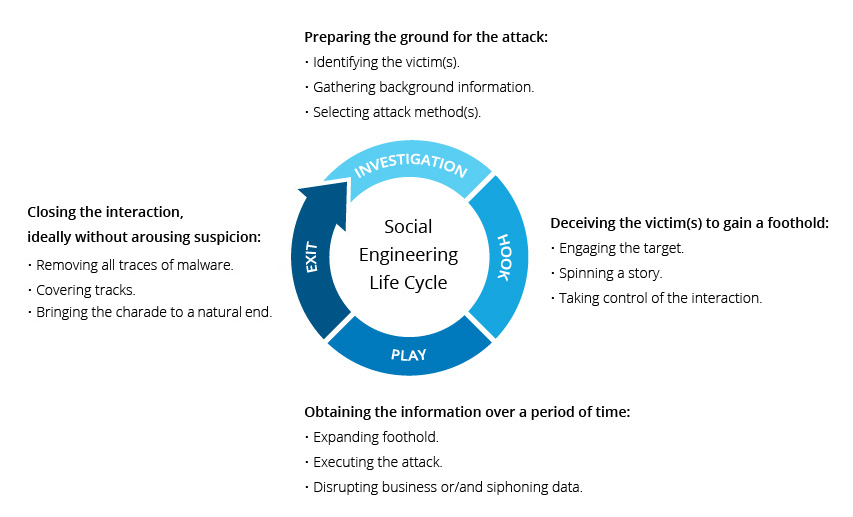
- Investigation – Collecting information to help identify potential entry points and weaknesses in corporate security protocols, departmental structure, and staff
- Hook – This stage is all about relationship building with the target after the requisite information has been acquired. The victim is manipulated with fake trust-building tricks.
- Play – Use information and relationships to infiltrate the target with intended attacks such as stealing corporate information, planting malware, or syphoning funds.
- Exit – After the goal is accomplished, close the interaction, and remove all the possible traces of the crime.
Common Social Engineering Attacks
Almost all cyberattacks, where human interaction is involved, have some form of social engineering in them. According to Verizon's 2021 Data Breach Investigations Report, 85% of breaches involved the human element, while social engineering was an integral part of 35% of those incidents.
Here we enlist the most popular social engineering attack techniques:
Phishing – involves an email or text message imitating a trusted source requesting sensitive information. The attacker sends fake email containing malicious link intended to steal your identity and confidential information. There are different forms of phishing:
Vishing – voice-based phishing
Smishing – SMS-based phishing
Spear phishing – targeted email phishing
Angler phishing – disguising as a company's customer service agent on social media to trick customers
Baiting – one of the most common social engineering attacks where attackers use a false promise and capitalise on the victim's greed or curiosity.
Pretexting – involves a false justification for a specific course of action – to gain trust and trick the victim. For e.g.: a simple online product survey form that asks for bank account details
Scareware – bombards victims with false system-damage alerts and prompts them to download malicious software for remediating that system issue.
Business Email Compromise (BEC) – fraudsters impersonate company owners or executives deceiving the recipient to perform illegal actions such as sending money to the attacker's account.
Tailgating – also referred as piggybacking. Social engineers pose as employees/ staff and follow authorized people into restricted areas.
How to Spot a Social Engineering Attack?
The approach of social engineering attacks varies for every victim and is primarily based upon the attacker's goals and the kind of information that can be extracted. The following section lists common, recognizable clues of a social engineering attack.
- Using fear as a stimulus: Attacker might send intimidating emails or texts posing to be from an authoritative entity leading them to take a certain action that involves sharing sensitive information. For example, a fake email from the income tax department insisting to fill and verify bank related information to avoid hefty penalties.
- Urgency: Social engineers craft their language to engender a sense of urgency in their victims. As a result, victims rush to divulge their details unknowingly. KYC update message with a deadline and service blockage warning is one of the most common ways to execute a social engineering attack.
- Inconsistency: Pay close attention to inconsistency in the emails received. Poor grammar, misspellings, and inconsistent formatting are other indicators of a possible phishing attempt.
- Unexpected messages and requests: Social media connection requests from someone you don't recognize or receiving an unusual request from someone asking specific information via suspicious links.
- Incomplete contact details: Social engineers will never provide correct contact details. They insist you to communicate through email or chat only. They refuse to share phone numbers and may lie that their systems are "down".
- Avoiding questions: When faced with unfamiliar questions, such attackers try to deflect the conversation and find a way to throw the questions back to the victim. Such evasions indicate the fabrication of a social engineering attack.
These are some of the prevalent red flags of a social engineering attack that one should watch out for. One needs to be on their toes when reading through emails and messages.
How to Avoid a Social Engineering Attack?
Since social engineering attacks are devised to leverage natural human traits like fear, curiosity, greed, respect, desire to help, etc., these security threats will never vanish no matter how robust a security system you have in place. They, however, can be substantially prevented by taking proactive ways.
Following tips can help improve your protection against a social engineering attack:
- Identify your critical assets and step up their security.
- Think before you click: Check the source and its legitimacy before clicking.
- Enforce multi-factor authentication (MFA) to add a layer of protection to the sign-in process.
- Slow down and do not get influenced by the urgency depicted in a message. Evaluate the source before rushing into anything.
- Keep confidential information and devices secured/ locked when not in use.
- Be suspicious of emails/ text messages/ calls from unsolicited people. Contact them directly to verify their authenticity.
- Beware of free downloads. They can be a carrier of hazardous malware.
- Do not overshare personal information on social media or other digital platforms.
- Be wary of irresistible offers. They are mostly fake. Delete such messages and do not entertain further.
- Set spam filters on HIGH. Keep a check on your email spam filter settings.
- Deploy trusted antivirus software, firewalls, and other security tools. Keep them updated always.
- Contact your cybersecurity/IT department about any suspicious online activity.
- Conduct regular Security Awareness Trainings to keep yourself and your employees stay abreast of evolving threats and the ways to defend them.
Conclusion
Social engineering attacks exploit human psychology and can wreak havoc on our devices and data. Social engineers are increasingly using sophisticated tactics to manipulate the human mind to commit these cybercrimes. Thus, without a doubt, social engineering attacks are bound to thrive with our growing digital footprint. While there is no permanent cure to a social engineering attack, by being fully aware of how it works and taking basic safety measures, we will be less likely to fall victim to such grievous cyberattacks.
References:
https://www.knowbe4.com/what-is-social-engineering/
https://www.verizon.com/business/resources/reports/dbir/
https://us.norton.com/internetsecurity-emerging-threats-what-is-social-engineering.html
https://www.cisco.com/c/en/us/products/security/what-is-social-engineering.html





